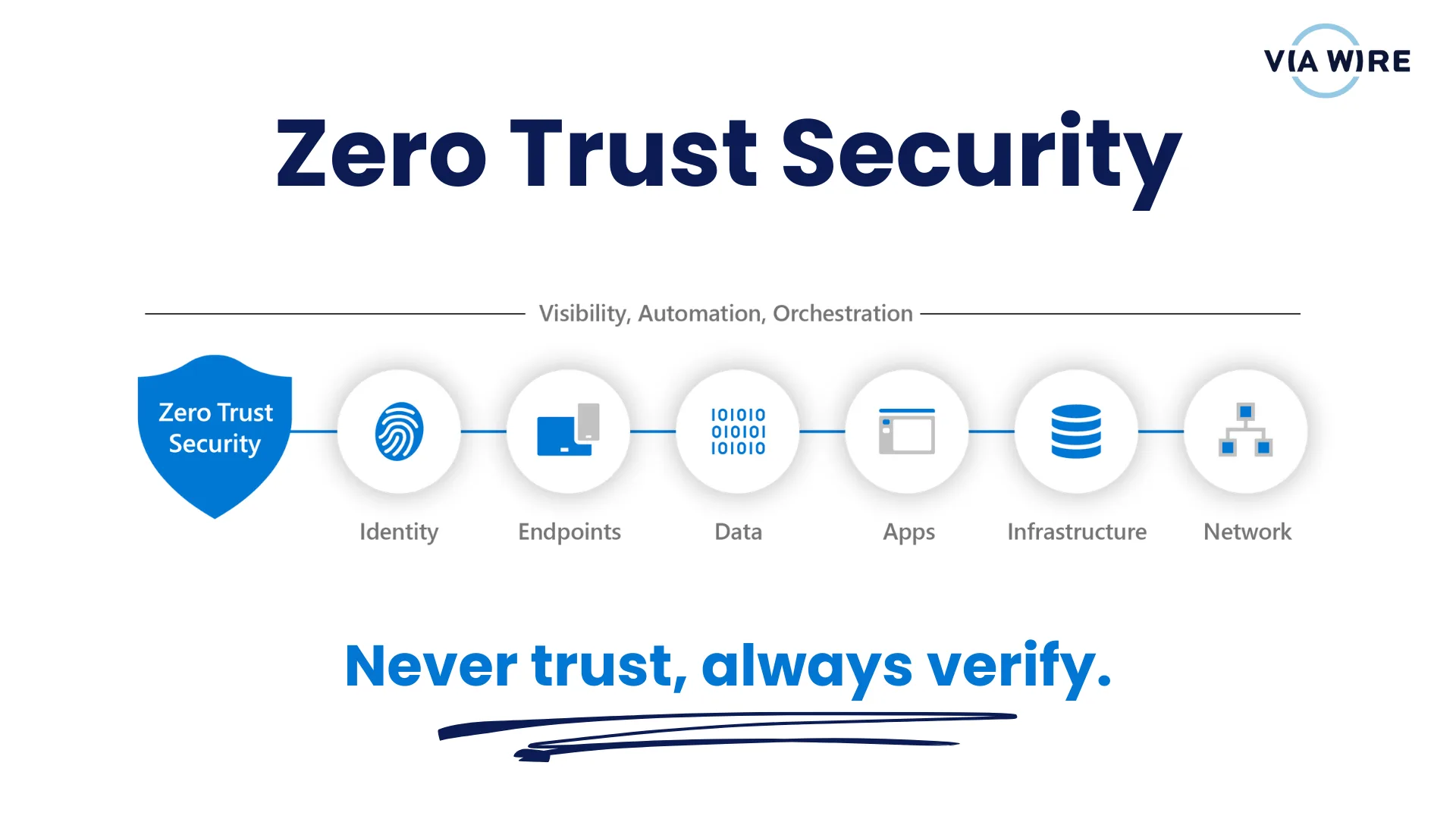
Zero Trust might sound like a big, complex security strategy reserved for large enterprises, but the truth is: small and medium businesses need it just as much — maybe even more. Cybercriminals increasingly target SMEs because they often have fewer security controls in place.
The good news? You don’t need an enterprise budget to take your first steps. In fact, three simple actions in Microsoft 365 can dramatically improve your security:
✅ Enable Multi-Factor Authentication (MFA)
✅ Review User Access
✅ Set Up Conditional Access Policies
Let’s break each one down.
—
1. Turn On Multi-Factor Authentication (MFA)
Relying on passwords alone is like locking your front door but leaving the window open. MFA adds another layer of protection by requiring something you know (your password) and something you have (a device or app).
Why the Microsoft Authenticator App Is Essential
When enabling MFA, you’ll be given options like SMS codes or an authentication app. While SMS might seem convenient, it comes with risks:
SIM-swapping attacks: Hackers can hijack your phone number and intercept codes.
Phishing: Fake websites can trick users into entering SMS codes.
The Microsoft Authenticator app is far more secure because:
- It uses secure push notifications and time-based one-time codes that can’t be intercepted like SMS.
- It works offline, so no mobile signal is required.
- It’s faster and easier — approve logins with a single tap.
Quick win:
- Enable MFA for all users via the Microsoft 365 admin centre.
- Make the Microsoft Authenticator app the default option.
—
2. Review User Access Regularly
Roles change, employees leave, but their access often stays the same. This creates unnecessary risk.
Quick win:
- Remove old accounts immediately.
- Apply the principle of least privilege — give users only the access they need for their current job.
Why it matters: Over-privileged accounts are a top target for cyberattacks.
—
3. Use Conditional Access Policies
Conditional Access brings Zero Trust to life by enforcing security rules based on context, such as:
- Where the user is logging in from
- Which device they’re using
- Whether the device is compliant
Example policy: Require MFA for logins from outside your normal locations or on unmanaged devices.
Quick win: Start with basic policies and expand over time.
—
Why These Steps Work
These actions align with the core Zero Trust principles:
- Verify explicitly
- Use least privilege access
- Assume breach
You don’t need to overhaul your entire infrastructure overnight. Start small and build a strong foundation.
—
✅ Need a hand? We can help you roll out MFA, deploy the Microsoft Authenticator app, and create Conditional Access policies tailored to your business.

0 Comments